Protect your iPhone against security threats with Avast One
- Security
- Privacy
- Performance
One of today’s most pressing cyberthreats, ransomware kidnaps your sensitive files and holds them hostage unless you pay up. To keep your files and data safe, learn what ransomware is, how it works, and how you can help prevent ransomware from infecting your devices with a world-class anti-malware tool like Avast One.

Ransomware is a type of malware that blocks access to files and computer systems while demanding a ransom payment in exchange for returning access. Ransomware uses encryption to block access to infected files, making them unusable and inaccessible to victims. Ransomware attacks target all kinds of files, from personal to business-critical.

This Article Contains:
The meaning of ransomware is just what it sounds like: ransom malware. After a ransomware attack, the hackers or cybercriminals responsible contact the victims with their demands, promising to unlock their computer or decrypt their files after a ransom is paid, usually in bitcoin or some other cryptocurrency.
Though awareness of the destructive potential of ransomware has been growing over recent years, ransomware attacks continue to plague individuals, businesses, and governments.
The first documented ransomware attack, known as the AIDS Trojan or the PC Cyborg, was launched in 1989 by Dr. Joseph Popp, a Harvard-educated evolutionary biologist. Dr. Popp stored his virus on floppy disks that appeared to contain an AIDS education program, then mailed the infected disks to his victims. Once activated, the AIDS Trojan encrypted files on the victim’s computer and demanded a ransom of $189 to unlock the files.
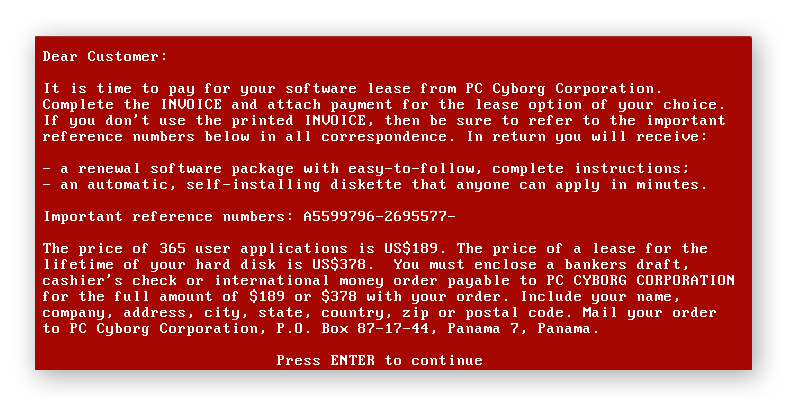 The AIDS Trojan ransomware note. (Source: Wikimedia Commons)
The AIDS Trojan ransomware note. (Source: Wikimedia Commons)
Today, attackers have easy access to open-source ransomware programs. Successful attacks can be extremely lucrative, netting some hijackers millions of dollars and forcing individuals, companies, or governments to clean up the mess. The potential rewards for cybercriminals have led to a surge in ransomware attacks over recent years.
That was especially apparent during the COVID-19 pandemic, which brought forth another spike that included cybercriminals hitting a string of hospitals with ransomware — making an already critical situation that much worse.
Ransomware can spread in several ways, including via malicious email links or attachments, phishing messages, and zero-day exploits. Using generic interpreters, hackers can create cross-platform ransomware that can do a lot of damage in very little time. New techniques like encrypting whole disks rather than selected files increases the scope of attacks.
Today, ransomware spreads even more easily, because with little or no expertise, hackers can use malware kits and ransomware as a service (Raas) to spread ransomware attacks and other malware.
Ransomware is spreading more than ever because hackers can use tools like ransomware as a service kits that easily distribute attacks. And ransomware payouts can be very lucrative, increasing incentives for attackers. The data held ransom can be extremely valuable — to an individual, business, or enterprise — and victims are often willing to pay a lot to get it back.
Some types of ransomware can infiltrate your device and encrypt your files without any action on your part, making the spread of ransomware even easier. Other ransomware attacks rely on more traditional methods of malware infection.
Here are different attack vectors that can spread ransomware:
Exploit kits: Malicious actors develop exploit kits to take advantage of vulnerabilities in applications, networks, or devices. This type of ransomware can infect any network-connected device running outdated software. Keep your systems and apps updated to shield your hardware and files from attacks.
Phishing: In a phishing attack, cybercriminals use social engineering techniques to impersonate trusted contacts and send you an email with a malicious link or attachment that’s often disguised as a fake order form, receipt, or invoice. In reality, these files (a fake PDF, XLS, DOCX file) are executable files in disguise: downloading and opening the file triggers the ransomware attack.
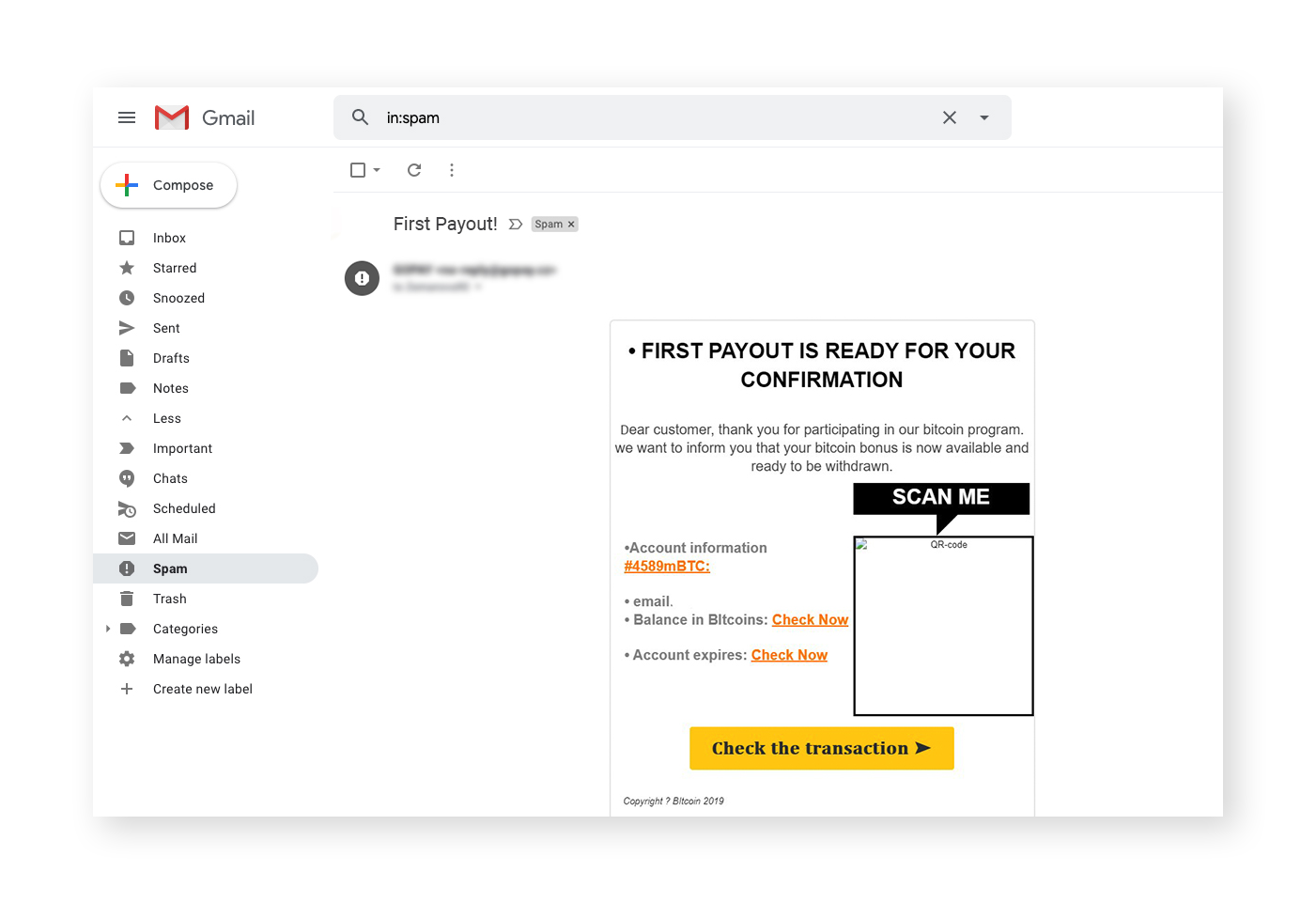 Phishing emails can include attachments and links that look authentic.
Phishing emails can include attachments and links that look authentic.
Malvertising: Attackers can distribute malware by embedding it in fake online ads in a practice known as malvertising. While some malvertising ads only install ransomware onto your device after you click, others download the ransomware as soon as you load the webpage — no clicks required. An ad blocker, such as the one in Avast Secure Browser, can protect you against these malicious ads.
Drive-by downloads: Attackers can seed websites with malware so that when you visit, the site automatically and secretly downloads the malware onto your device. If you’re using outdated browsers and apps, you’re especially vulnerable to this technique, but a free antivirus app can help.
Ransomware attacks may not begin immediately. Some ransomware is designed to lie dormant on your device to keep you from identifying its source. The AIDS Trojan strain didn’t activate until the infected computers rebooted for the 90th time.
A ransomware attack works by encrypting files or locking up your entire device. Then, a ransom note usually appears on your screen demanding money in exchange for a decryption key.
Here’s how a ransomware infection works:
The ransomware encrypts your files. Malicious code in the ransomware scrambles files or file structures so they become unusable and inaccessible until you decrypt them. Ransomware tends to use data encryption methods that can only be reversed with a specific decryption key, which is what the ransomware attacker is asking you to pay for.
Then, a ransom note appears on your screen after the malware encrypts your files. This note is how a ransomware attacker tells you how much to pay, how to transfer the ransom, and the deadline. If the deadline passes, the ransom fee may increase, or the attacker may threaten to permanently encrypt or delete your files.
Once the ransomware is on your device, any attempt to open your encrypted files will most likely result in a critical error message informing you that your files are corrupt, invalid, or cannot be located. And it’s not just Windows users who can be infected with ransomware — ransomware can affect Macs and mobile devices, too.
Ransomware attacks use asymmetric encryption, which involves the creation of two encryption keys: a public key to encrypt the data and a private key to decrypt it. The attacker generates a unique key pair and places the public key in the malware, encrypting the victim’s data. Once the demand for payment is met, the attacker promises to send the private key for decryption.
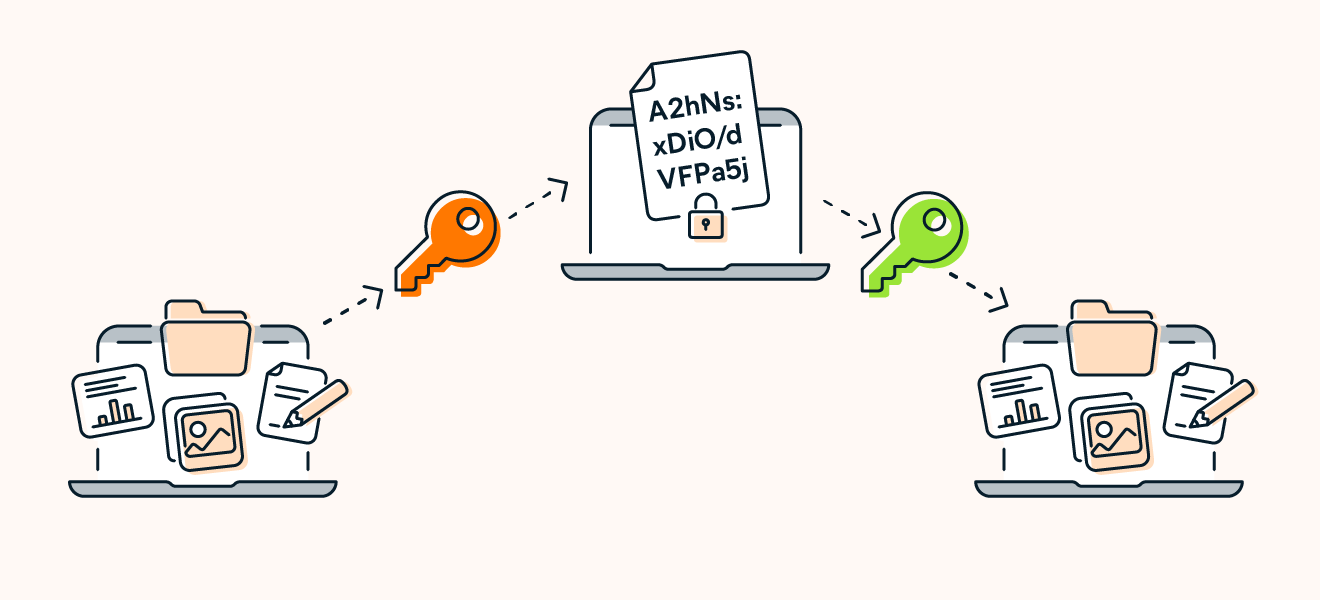 Ransomware attacks use asymmetric encryption: a public key encrypts files and a private key decrypts them.
Ransomware attacks use asymmetric encryption: a public key encrypts files and a private key decrypts them.
Keeping your system updated is critical to prevent ransomware threats from exploiting your system’s vulnerabilities. By practicing smart internet habits and using a reliable ransomware prevention tool, you can help prevent a ransomware attack.
Our dedicated guide on ransomware prevention has details about how to stay safe. In the meantime, here are a few tips to help you prevent a ransomware attack:
Keep your software updated. Making sure your OS and apps get new updates as soon as they’re released will plug security holes and prevent hackers from using exploits to deploy ransomware.
Back up your system regularly. Ransomware works by blocking access to your files. If your files are backed up elsewhere, you likely won’t have to pay a ransom. Perform regular backups of your system and files using cloud services or physical storage options. And schedule automatic backups, if your device allows it.
Use an ad blocker. Load up your browser with one of the best ad blockers to shield yourself from malvertising links and drive-by downloads: two ad-related ways ransomware can target your system.
Be skeptical. Be wary of strange links sent in emails or on other messaging platforms. Even if the link comes from someone you know, they could have been hacked. Learn how to identify and avoid visiting unsafe websites.
Use an antivirus. Ransomware can hurt you only if it can reach you. Use a robust cybersecurity app that blocks malware and viruses before they can get near you. Avast One offers real-time security protection, blocking unsafe links, malicious downloads, and unsecure websites. Start protecting yourself today.
Different types of ransomware attack range from annoying to life-threatening. Some ransomware locks you out of your computer, while others can eradicate your files and render your operating system useless. All types of ransomware, by definition, have one thing in common: a ransom demand.
While new strains of ransomware are always in development, here’s an overview of the main types of ransomware:
Filecoders: Also known as encryptors, filecoders make up 90% of ransomware strains. Filecoders encrypt and lock files on infected devices. The attackers demand payment for decryption keys, usually by a deadline after which they may damage, destroy, or permanently lock your files.
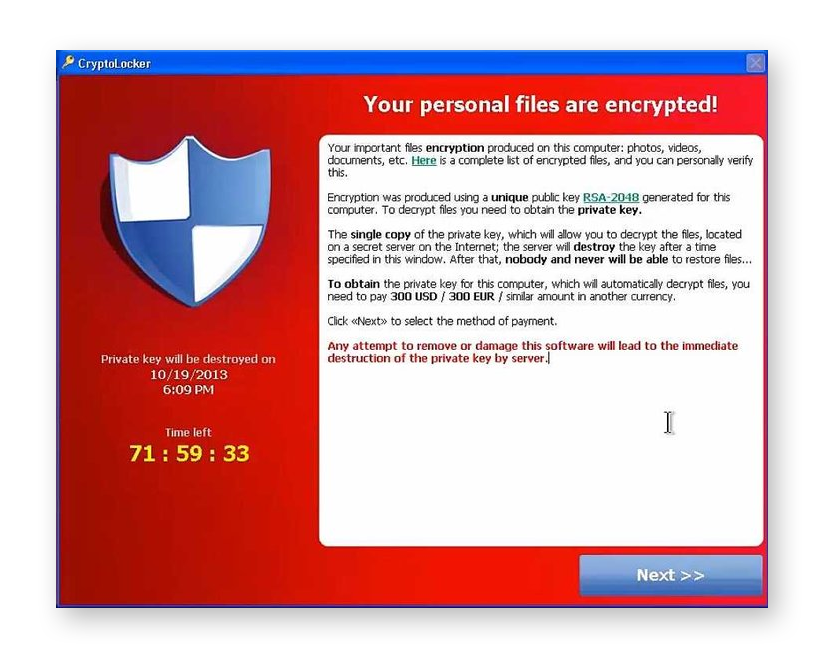 The CryptoLocker ransomware note. (Source: Nikolai Grigorik, Wikimedia Commons)
The CryptoLocker ransomware note. (Source: Nikolai Grigorik, Wikimedia Commons)
Screenlockers: These lock you out of your device completely. Screenlockers tend to mimic government institutions, like the US Department of Homeland Security or the FBI, and inform you that you broke the law and must pay a fine to unlock your device.
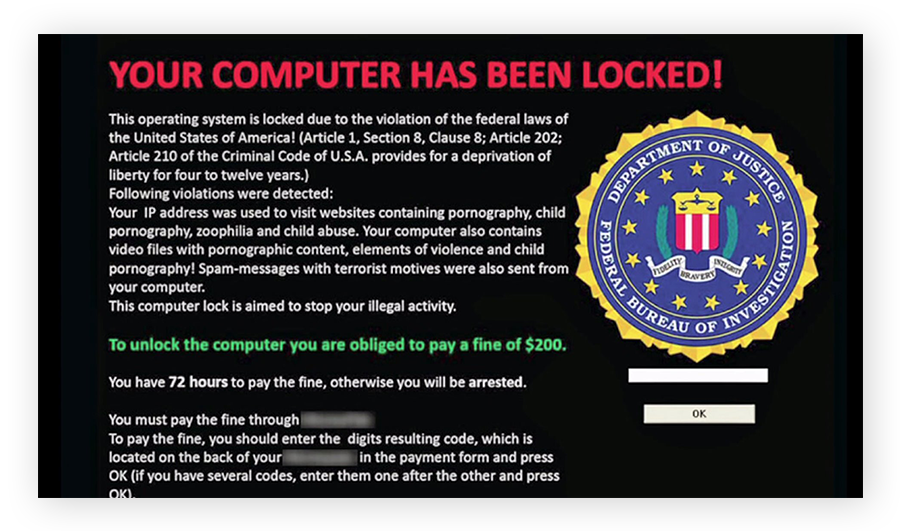 A screenlocker ransomware example. (Source: Motormille2, Wikimedia Commons)
A screenlocker ransomware example. (Source: Motormille2, Wikimedia Commons)
Doxxing: Doxxing is not technically a form of ransomware, but it is a serious digital threat that can involve a ransom demand. Through a malicious file or link, the attacker gains access to your private data, including usernames, passwords, credit card numbers, and passport details.
You then get a message telling you that unless you pay a fee, your attacker will publish your information. Our free Avast Hack Check tool can tell you whether your passwords have leaked or been stolen. For stronger protection, get an advanced identity theft monitoring tool.
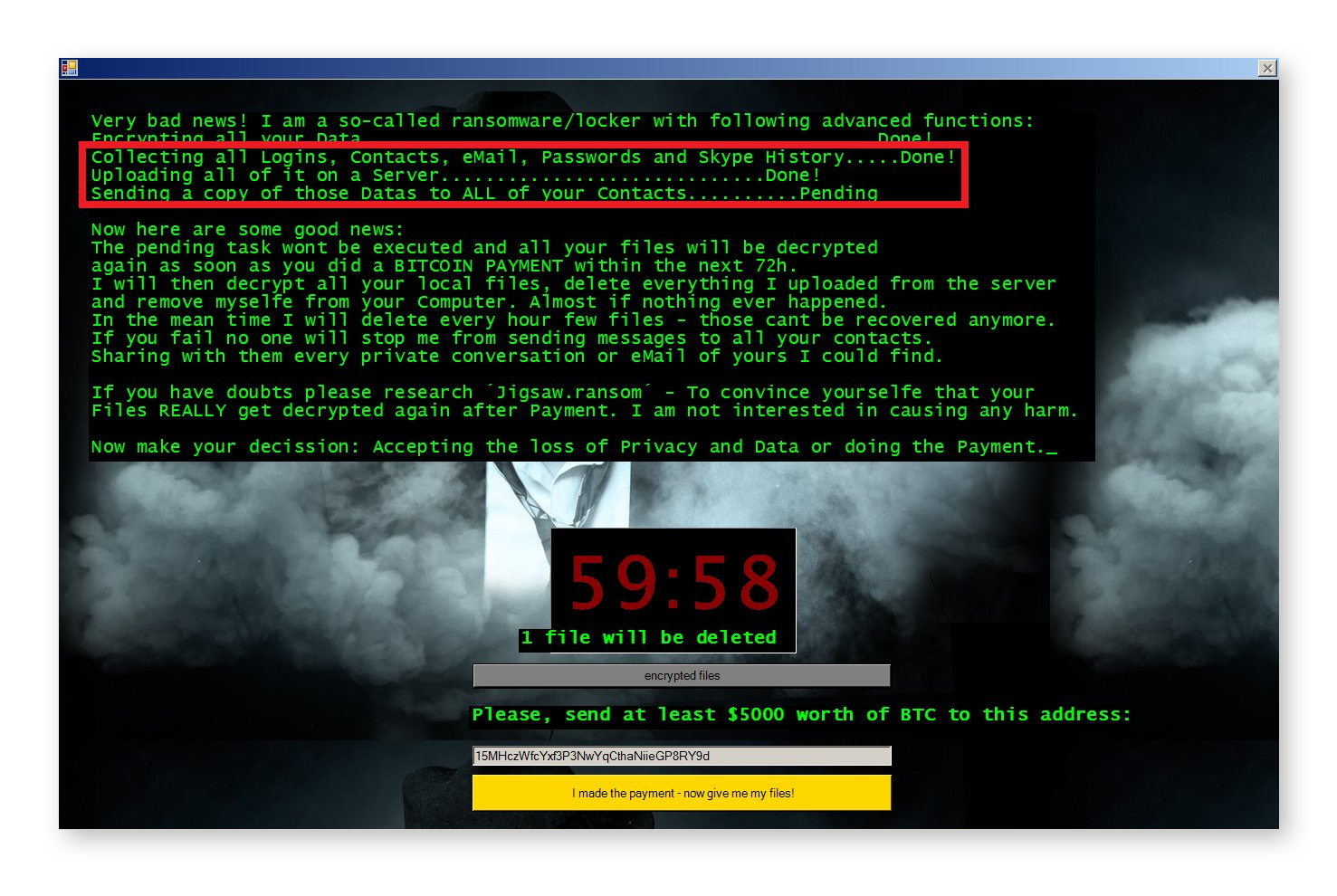 An example of a malware-based doxxing threat. (Source: Jakub Křoustek)
An example of a malware-based doxxing threat. (Source: Jakub Křoustek)
Scareware: Scareware is a fake software program that claims to have found issues on your computer and demands payment to fix them. Scareware typically bombards your screen with pop-ups and alert messages. Some strains behave more like screenlockers, locking up your computer or mobile device until you pay.
Ransomware’s rise in popularity is due in part to its availability and ease-of-use. Criminals can buy customizable open-source tools that let them launch new malware attacks. And hackers are constantly updating their code to strengthen their encryption, giving new life to older ransomware strains.
The majority of ransomware attacks target Windows PCs. But Macs, iOS devices, and Android devices have all been hit. The following sections look at examples of the biggest ransomware attacks that criminals have deployed over the years.
Windows PCs are still the most popular targets for computer ransomware attacks. Malicious hackers can often exploit Windows-specific vulnerabilities relatively easily, and there are a lot more PC users than Mac users. Many of the most well-known ransomware strains are currently inactive because software updates have patched the vulnerabilities they targeted. But new strains always emerge.
The WannaCry strain shows how extensive a PC-based ransomware attack can be. In May 2017, WannaCry spread across the globe, ultimately attacking over 100 million users while causing hundreds of millions of dollars in damage.
Emerging in 2018 and estimated to have affected over 1.5 million users, the GandCrab family of ransomware was nullified in 2019 thanks to a coalition of state and private cybersecurity researchers. GandCrab operated on a ransomware as a service (RaaS) model. With the decryptor now freely available online, GandCrab is fortunately no longer a critical threat.
The Petya strain, which first appeared in 2016 and returned in a more advanced form in 2017, uses the screenlocker approach by encrypting your hard drive’s master file table to lock up your computer. Some versions came bundled with a secondary strain of ransomware known as Mischa, a conventional filecoder that took over if Petya couldn’t activate on a victim’s computer.
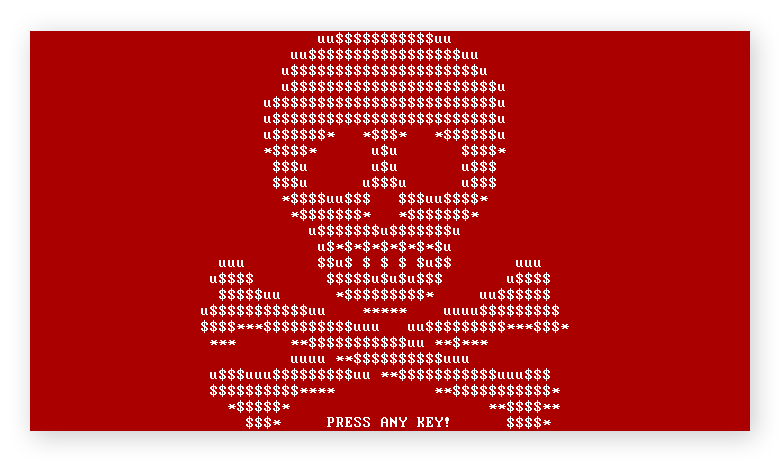 A screenshot of Petya ransomware attack (Source: Wikimedia Commons)
A screenshot of Petya ransomware attack (Source: Wikimedia Commons)
Since ransomware attackers maximize their profits by spreading to many devices, they’ve started encouraging victims to infect others. The Popcorn Time strain asks you to infect two other users with the malware in lieu of paying a ransom. If both of those users pay the ransom demand, you will receive your files back — free of charge.
The Locky ransomware threat usually spreads through fraudulent emails with malicious attachments. Once opened, your files are locked tight. Locky can encrypt a variety of files, from Microsoft Office files to your computer’s actual source code. Locky was most prominently used in 2016 for a campaign targeting healthcare institutions.
The CryptoLocker ransomware strain is especially nasty. It infects itself within a PC user’s profile and scans the computer, any connected devices, and devices on its network for files and folders to encrypt. Appearing in late 2013, CryptoLocker used the notorious Gameover ZeuS botnet to spread in a sustained campaign that lasted for months.
Using the RaaS model, the creators of Cerber licensed their strain to other cybercriminals for a percentage of earnings from their victims. Introduced in 2016, Cerber became a very popular ransomware option due to its ease-of-use and availability. It’s still a prevalent threat today.
Ryuk is ransomware that targets high-value victims likely to pay big ransom demands. Targets include: businesses, governments, and public institutions like hospitals and schools. First appearing in 2016, Ryuk isn’t slowing down. In 2021 a new variant emerged, capable of using computer worms to spread between devices and networks without human interaction.
From online banking credentials to social media details, smartphones contain a trove of private data. Hackers have taken notice and are increasingly targeting mobile devices for cyberattacks — including ransomware.
Ransomware often makes its way onto Android devices through third-party download portals. But there have been cases where ransomware was hidden within seemingly legitimate apps in Google Play. If you are targeted, learn how to remove ransomware from Android.
If you’re an iPhone user, you may not need to remove ransomware from iOS, but you should look out for “fake ransomware” that can trick you into paying a real ransom demand.
Apple devices are generally less susceptible to malware attacks, but their growing user base has gained them more attention from malware developers.
In 2017, two security firms uncovered ransomware and spyware programs that specifically targeted Apple users. Researchers determined that software engineers who specialize in macOS developed these programs and made them available for free on the dark web.
Recently, there have been some ransomware attacks targeting Apple, though none of them have resulted in a significant outbreak. More commonly, malicious attackers have accessed Mac iCloud accounts and used the Find My iPhone service to launch screenlocker attacks.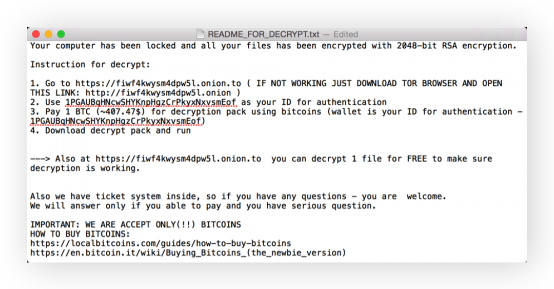 An example of an Apple screenlocker ransomware. (Source: Jacklafo via Wikipedia)
An example of an Apple screenlocker ransomware. (Source: Jacklafo via Wikipedia)
Regardless of what device you have, use a VPN and firewall when you browse online. Together, these safeguards can help protect you against all kinds of online threats by encrypting your connections and filtering out malicious traffic. When in doubt, connect to the web via VPN, proxy, or Tor to make your connection as private as possible.
Ransomware as a service is what less tech-savvy hackers use for ready-made ransomware attacks. RaaS is an economic model where developers can create and sell ransomware without actually distributing it. Those who purchase and use RaaS pay a percentage of the final take to the developer of the malware.
Some RaaS is subscription-based; other types require registration to gain access to the ransomware programs.
Ransomware is not a virus, but it is a form of malicious software. The term virus is commonly used to refer to all forms of malware. But, a computer virus is just one type of malware, and each type of malware behaves differently.
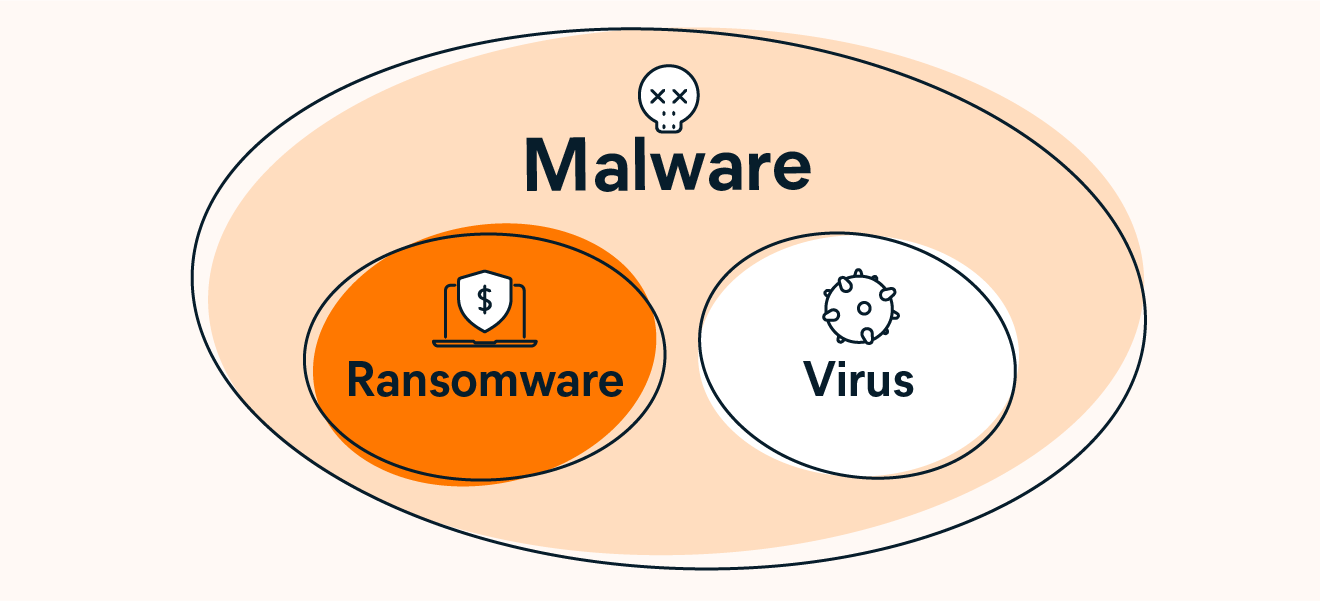 Ransomware and viruses are two different types of malware, but they aren’t the same.
Ransomware and viruses are two different types of malware, but they aren’t the same.
Viruses, worms, and trojans can all be delivery methods for ransomware. Although the term “ransomware virus” is technically incorrect, ransomware could be spread using a virus.
Our research suggests that trojan malware is the most common way to spread ransomware — meaning the threat is hidden inside a file or link that looks both harmless and important enough for you to open. When ransomware is delivered via a computer worm, it spreads automatically, like WannaCry, or it can spread via the user, like Popcorn Time.
Depending on your device and the strain, you may be able to get rid of ransomware. The ransomware removal process is the relatively easy part, but recovering your encrypted files can be impossible — sometimes even after the ransom demand has been paid.
Removing the ransomware from your device is not a guarantee that you will succeed in negating its effects. If you’re struggling with ransomware, consult our guides to removing ransomware from PC and removing ransomware from Mac.
If you’re looking for a way to unlock files after a ransomware attack, you might find the solution you need in this list of Avast ransomware decryption tools.
We strongly recommend that you don’t pay the ransom or attempt to negotiate with your attacker. Giving in to their demands will only inspire cybercriminals to continue developing and launching new ransomware strains to steal from others. These attackers could also be using their ill-gotten gains to fund other illegal activities. The US Federal Bureau of Investigation also “does not support paying a ransom in response to a ransomware attack.”
 If you get hit with a ransomware virus, our advice is not to pay the ransom.
If you get hit with a ransomware virus, our advice is not to pay the ransom.
Paying the ransom doesn’t guarantee that your attacker will delete the ransomware or unlock your device. Some hijackers have collected ransoms and disappeared or sent useless decryption keys. You could even end up paying a completely different ransomware attacker.
If you can’t recover your files following a ransomware attack, hold out for a decryption tool. Sometimes, there’s a flaw in the cryptography the ransomware code uses, and the malware exposes lines of code that allow cybersecurity researchers to develop a fix.
It takes just one click to inadvertently download ransomware. Once you do, it’s usually too late to fight back — unless you’ve already installed a strong anti-ransomware program. Fortify your device’s defenses with the powerful ransomware shield built directly into Avast One.
Avast One will alert you to any signs of ransomware and other malware, and it will remove the malicious code from your device before it can infect it. Protect your most important files with the award-winning, free cybersecurity engine trusted by more than 400 million people worldwide.
Here are some frequently asked questions about ransomware.
There are several vectors for ransomware attacks — one of the most common is phishing emails. Here, a victim receives an email with an infected attachment or link. Once the email attachment is opened, the ransomware is initiated and starts to seize data. Cybercriminals can target victims randomly, or they can target specific individuals with tailor-made attacks.
You can reduce your exposure to ransomware attacks by limiting the amount of personal information you share online, never clicking suspicious links or opening unknown email attachments, and only downloading software from trustworthy and verified sources. You should also keep your programs and operating system updated and use a dedicated ransomware protection tool to help secure your device and files.
Ransomware recovery is the process of restoring files, devices, or systems following a ransomware attack — ideally with the help of ransomware decryption tools that let you regain direct access to the data held hostage. Or, you may be able to recover from a ransomware attack if you have up-to-date backups stored on secure cloud infrastructure or an external SSD or HDD.
You can reduce your exposure to ransomware attacks by limiting the amount of personal information you share online, never clicking suspicious links or opening unknown email attachments, and only downloading software from trustworthy and verified sources. You should also keep your programs and operating system updated and use a dedicated ransomware protection tool to help secure your device and files.
Ransomware recovery is the process of restoring files, devices, or systems following a ransomware attack — ideally with the help of ransomware decryption tools that let you regain direct access to the data held hostage. Or, you may be able to recover from a ransomware attack if you have up-to-date backups stored on secure cloud infrastructure or an external SSD or HDD.
Yes, ransomware can steal data — though by definition, ransomware functions by locking out data until a ransom is paid. It’s common for hackers to hold onto private data held ransom even after the victim pays — effectively stealing the data. They can then use the data to launch more attacks or sell it online.
Yes, hackers use ransomware as a form of malware that lets them carry out a host of malicious activities, namely seizing your data until you pay a ransom. Ransomware is more readily available now than ever, because ransomware as a service (RaaS) enables less tech-savvy hackers to rent or purchase ransomware kits from malware developers.
Major ransomware attacks have made headlines due to their scale and impact. In 2017, the WannaCry ransomware strain successfully targeted over a 100 million users and caused millions of dollars of damage. The attacks hit major businesses and hospitals across the UK, taking control of several industrial processes until ransoms were paid.
“The threat actors responsible for this malware generally rely on spreading through the use of third party app stores, game cheats, and adult content applications. A common infection technique is to lure users through popular internet themes and topics – we strongly recommend that users avoid attempting to download game hacks and mods and ensure that they use reputable websites and official app stores.”
Ondřej David, Malware Analysis Team Lead & Jakub Vávra, Threat Operations Analyst
Download free Avast One for Windows PC to block ransomware and other malware. Get fast, real-time protection.
Download free Avast One for Mac to block ransomware and other malware. Get fast, real-time protection.
Install free Avast One for Android to block ransomware and other malware. Get fast, real-time protection.
Install free Avast One for iOS to get dedicated security protection for iPhone and iPad.
Protect your iPhone against security threats with Avast One
Protect your Android against ransomware with Avast One