Protect your Android against hacking and malware with Avast One
- Security
- Privacy
- Performance
Lit only by the soft glow of their monitor, a hooded figure inputs keyboard commands with blazing speed. Is this what comes to mind when you hear the term “hacker”? You might be surprised to learn that there are many different types of hackers, so keep reading to learn all about hacking and how to protect yourself from being hacked with a top-rated security solution like Avast One.

Hacking is the application of technology or technical knowledge to overcome some sort of problem or obstacle. Note that our hacking definition intentionally doesn’t include anything criminal. While many hackers can and do apply their skills to nefarious ends — and while many folks associate hacking with criminal or security hacking —that’s just one part of the bigger picture.

This Article Contains:
There are many types of hacking out there, but in this piece, we’ll focus on the world of computer hacking. Depending on who you ask, you’ll get two different answers when it comes to defining hacking in this sense:
Traditionally, a computer hacker is a skilled programmer who is immersed in computer and software culture.
But many of us tend to think of hackers as criminals who gain access to computers or networks by breaking through security measures. That is usually what the media means when it uses the term “hacker.”
Traditional hackers refer to the criminal subversion of a security system as “cracking,” as when a bank robber cracks a safe. So what’s a hacker? Simply put, a hacker is someone who applies their computer skills toward solving a problem.
Depending on their motivations, there are three types of hackers: black hat, white hat, or grey hat. Let’s take a look at who they are and what distinguishes them from one another.
A black hat hacker is the shady cybercriminal described above. They’re the ones cracking through cybersecurity systems to gain unlawful access to a computer or network. If a black hat hacker discovers a security vulnerability, they’ll either exploit it themselves or alert other hackers to the opportunity, typically for a price.
Most of the time, the ultimate goal of a black hat hacker is to make money, whether through direct financial theft, the sale of compromised information, or extortion. But sometimes, they’re simply looking to cause as much chaos as they can.
White hat hackers are the counterparts to the black hats. They’re just as skilled, but rather than pursuing criminal ends, these kind souls apply their talents toward helping businesses shore up their digital defenses. A white hat hacker will intentionally attempt to crack a system, with permission from its owner, in order to identify weak points to be repaired. This type of work is also known as “ethical hacking.”
Many white hat hackers work in-house at large companies as one part of the organization’s larger cybersecurity strategy. Others offer their services as consultants or contractors, hired to test a company’s security. They may go beyond penetration testing — evaluating the strength of a cybersecurity system — to also test employees themselves with phishing campaigns aimed at securing their login credentials.
Between those two sit the grey hat hackers. They’re not quite the paragons of altruism that white hat hackers are, nor are they dedicated to criminal acts. Where white hats obtain permission before probing a system for vulnerabilities, grey hats skip that part and head straight to the hacking.
Some grey hats behave like mercenaries, discovering weaknesses and then approaching the business to offer their services at a fee. Others hack in order to force a reluctant business to take action against a certain vulnerability. A notable instance of grey hat hacking in 2013 resulted in Facebook having to acknowledge and repair a security flaw after it previously ignored the hacker’s warnings.
We can identify several types of computer hacking by dissecting security breaches. Individuals, private hacking collectives, companies, and governments all engage in security hacking when it suits their needs or desires. Let’s take a look at three of the most prevalent types of hacking.
Lone black hat hackers as well as hacking collectives are typically thieves. Their cybercrimes are targeted at either directly stealing money, enabling later theft via data hijacking, or selling the acquired data to other cybercriminals.
If a hacker can obtain your user credentials, or even a few bits of personal information, they can attempt to crack your password or ensnare you in a phishing trap. Either way, the end game is to turn your money into their money.
Data breaches are a frequent example of financially-motivated hacking. Hackers break into a website’s servers, capture data about the site’s users, and then sell what they’ve stolen. In 2017, the US credit bureau Equifax announced that it had suffered a gargantuan data breach affecting over 147 million people.
The leaked data included not just full names and birthdays, but also social security and driver’s license numbers, as well as hundreds of thousands of credit card details. The loss of that much valuable data left many customers vulnerable to identity theft and fraud.
With so many industries as cutthroat as they are, it’s unsurprising that companies are often willing to get dirty to triumph over the competition. Corporate (or industrial) espionage is the commercial application of hacking, malware, phishing, and other unsavory spying techniques to obtain privileged insider information from a business competitor — aka information hacking.
Sometimes, it’s as simple as poaching a disgruntled employee, but in other cases, more tech-savvy solutions are in order. In 2017, US prosecutors indicted three people connected to the internet security company Boyusec (or, more fully, Guangzhou Bo Yu Information Technology Company Limited) for corporate hacking. The three hacked into various companies, including Moody’s Analytics and Siemens, to siphon off trade secrets and protected intellectual property.
Cybersecurity researchers would later link Boyusec to the Chinese hacking group APT3 or Gothic Panda, which itself is alleged to have ties to China’s Ministry of State Security — bringing us neatly to the third installment in our trilogy…
The potential rewards from security hacking can be so great, even governments want to get in on the party. Countries all across the world are constantly playing games of cat-and-mouse cyber warfare with one another. Everyone knows that everyone else is doing it, and everyone acts surprised and offended when they get caught.
Sometimes, governments (and state-supported hacking groups) will directly attack other governments. There are also concerns that governments might use state or private companies for offensive operations in foreign countries, which is why Huawei or Kaspersky have been flagged as potential security risks. But more commonly, you’ll see state-backed hackers targeting corporations, institutions such as banks, or national infrastructure networks.
In July 2019, Microsoft acknowledged that over the previous year it had informed nearly 10,000 people that they had been the targets of state-sponsored hacking attempts. The majority of the attacks were linked to groups thought to have ties to Russia, Iran, and North Korea. State-sponsored hacking is notoriously hard to prove, as governments typically distance themselves from the hacking via the use of proxy groups.
The concept of hacking as a philosophy goes way back to before the invention of the computer. The desire to experiment with something — to bend and manipulate it, to push it past its intended limits, and, in some cases, to demonstrate that it can be broken — is inherent to the human experience.
As computers emerged, it was only natural that someone would view them not simply as a tool for daily use, but as a challenge to be surpassed, or perhaps even as a playground.
The term “hacking” as it relates to technology first emerged in the 1950s at MIT, where it was used by members of the Tech Model Railroad Club to refer to the process of creatively solving a technical problem in an innovative way. In the 1960s, these students migrated from trains to computers, bringing their passion for inventiveness with them to extend the potential of this new technology.
In the 1970s, people hacked the phone system. Dubbed “phreakers” — as in “phone freaks” —these telecoms enthusiasts spent hours exploring phone networks to understand how things were interconnected before innovating their own exploits. They handcrafted devices known as “blue boxes” to aid in their phreaking adventures. Before having success with Apple, Steve Wozniak and Steve Jobs were both passionate members of the phreaking community.
With the introduction of the personal computer in the 1980s, hacking blossomed. Now, anyone with a computer at home could enter the hacking community. Sadly, it was inevitable that as more and more computer owners discovered their latent hacking talents, some of these people would apply them to nefarious ends — leading in 1986 to the passing of the world’s first anti-cybercrime legislation, the Computer Fraud and Abuse Act in the US.
At its most wholesome, hacker culture is a celebration of creativity and technological aptitude. Hackers of all ages are driven to experiment and explore, to approach technology from alternate perspectives, to answer the eternal question, “What if?”
In the same way that famed mountain climber George Mallory responded to a question about why he wanted to summit Mount Everest — “Because it’s there” — so too do hackers seek to demonstrate their skills by overcoming the technological challenges before them. When you hear people talking about making everyday experiences more convenient with “life hacks,” they’re using the term in this spirit.
Even if there’s nothing malicious behind the hacking, this drive can often land hackers in trouble. Large organizations tend to disapprove of people breaking into their supposedly secure systems without prior consent, and they’ll often pursue legal remedies to make an example out of hackers who penetrate too far.
Whether or not hacking is cybercrime depends on one thing: consent. White hat hackers get permission from their targets before hacking into systems, and they’re obligated to disclose any vulnerabilities they find. Outside of this context, security hacking is illegal.
Criminal hackers operating without consent are breaking the law. No one’s going to grant permission for a hack if you disclose up-front that you’re after their money or valuable trade secrets, so black hats do it all on the sly. Even grey hat hacking can be dangerous if your target decides to report you to the authorities after you disclose the hack.
It goes without saying that if you are the victim of a security hack, that’s most definitely illegal. If that ever happens to you, be sure to report the scam or hacking event immediately. You could help both reduce the damage done to you as well as prevent future victims from being hacked.
Given enough time and resources, there’s no way of knowing what a skilled hacker will be able to achieve. Plenty of multinational companies have been humbled at the hands of a motivated hacker determined to crack their security measures, no matter how stringent.
But considering the sorts of devices available in a typical home or office, there are certainly a few that are much easier targets than others. While your iPhone will prove extremely resilient, the same can’t be said for many of the other consumer-level digital devices. Here’s a short list of some of the most at-risk devices you might own:
Smart devices: Many devices in the Internet of Things lack the same comprehensive security protections that are either built into or available for computers and mobile devices. If a hacker obtains your data in a breach, they can use what they find to slide into your smart network and bounce from one device to another.
Routers: You’d be surprised to learn how many people don’t change the default login credentials on their router. Maybe you’re one of them. Hackers know which devices ship with which logins, and they can and do test Wi-Fi networks to see if those credentials still work. Routers and smart devices are especially vulnerable to botnet malware, which can include them in a distributed denial of service (DDoS) attack.
Webcams: If you’re still using a separate webcam, it’ll have the same vulnerabilities as any other IoT device. Laptop users are also at risk from rootkits, a type of malware that can allow hackers to access a device at any time, including the user-facing camera. It’s never a bad idea to stick some opaque tape over that lens.
Email: Sure, it’s not a device, but email is a frequent hacking target nonetheless. Passwords get leaked all the time in data breaches, and if you use the same password for your email as you use for other services, you’re letting hackers waltz right in.
Jailbroken phones: iOS devices and, to a lesser but still admirable extent, Android devices are very hack-resistant. If you’ve jailbroken yours — if you've removed the manufacturer’s built-in security measures — you’ll be very vulnerable to hacking, unless you know exactly which countermeasures to take.
To prevent hackers from getting on your network or in any of your devices, you should use a robust cybersecurity tool like Avast One. Avast uses six layers of protection, plus cloud-based artificial intelligence, to block 1.5 billion malware attacks every month. Detect weaknesses in your home Wi-Fi, shore up unsafe settings and weak passwords, and prevent phishing scams and viruses — all for free.
“My account was hacked!” Anytime something goes wrong on social media, this defense is a celebrity’s best friend. If you’re not careful with your passwords, it’s very easy for a hacker to gain control over one of your accounts. Once they’re inside, they can post on your behalf, access private content, and communicate with your contacts.
Want to check if any of your social media or email accounts have been leaked? Visit our free HackCheck tool to scan for any leaked passwords.
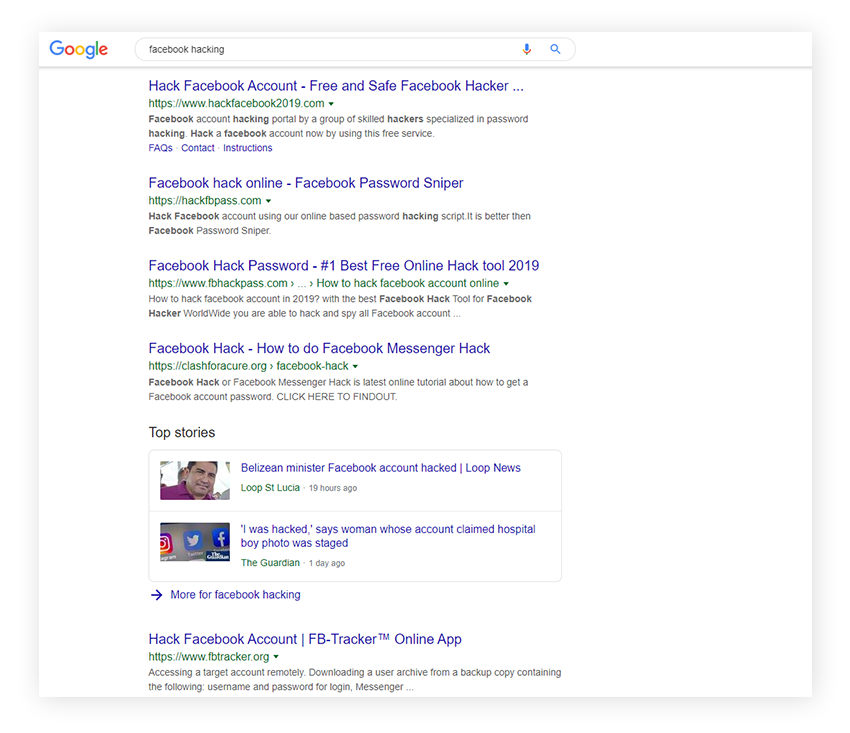
How prevalent is social media hacking? Google “Facebook hacking,” for example — as I did in order to find relevant news stories to share in this piece — and instead of articles, you’ll get a list of Facebook hacking tools. Of course, we highly discourage you from repeating this experiment or visiting any of the links you’ll find.
 Twitter hacking and Instagram hacking are also popular cybercrime activities. Twitter’s help page for hacked accounts suggests a password reset as the primary fix, echoing the need to maintain unique passwords for every service you use. If a hacker obtains one, they’ll be able to get into only that one account of yours.
Twitter hacking and Instagram hacking are also popular cybercrime activities. Twitter’s help page for hacked accounts suggests a password reset as the primary fix, echoing the need to maintain unique passwords for every service you use. If a hacker obtains one, they’ll be able to get into only that one account of yours.
Depending on the type of malware a hacker is using, the signs of hacking may differ from one instance to the next. Here’s a brief list of what you might see if there’s a hacker out there who’s infiltrated one of your devices:
You’re locked out. If a hacker gets ahold of your login credentials, they may change your password so that you can’t access your account anymore. In that case, initiate a password reset immediately and activate two-factor authentication (2FA) if it’s available.
Your device is working differently. Does your computer or mobile device feel like it’s changed out of nowhere? Have you noticed different passwords, drastically altered settings, new files, or strange changes to files you already had? Has your antivirus software been deactivated? Are any new programs or apps launching by themselves? Is your webcam or microphone turning on even when you’re not using it? Any one of those signs may point to a hacker.
Your socials are going haywire. If your family, friends, and colleagues begin alerting you that they’re receiving messages from you that don’t seem normal, change your passwords ASAP. The same goes if you notice any content on your social media feeds that you didn’t post yourself. Those are two common signs of a social media hack.
The hacker tells you. A ransomware note on your computer is a surefire sign that you’ve been hacked. The hacker may also contact you directly to let you know that they’ve compromised your devices and/or obtained a bit of your confidential information. Be aware, however, that an extortion attempt could also be a bluff, especially if the hacker hasn’t shown you any hard evidence of the dirt they claim to have on you.
Your browser is misbehaving. There are a lot of hacking tricks that work via your browser. Involuntary redirects — when you try to go to one page but are taken to another instead, without intending to go there — are a good sign that there’s something shifty going on. Also look out for toolbars and extensions that you didn’t add yourself. Lots of those occurrences are malware-based.
You’re drowning in pop-ups. Adware and scareware both make liberal use of pop-ups to grab your attention. A sudden glut of pop-ups is a dead giveaway that a hacker’s placed some malware on your device.
Someone’s spending or stealing your money. If you notice charges popping up, and you haven’t bought those items or services, get in touch with your financial institutions right away to freeze your accounts and credit cards. The same goes for a sudden drop in your bank balance. Thanks to a hacker’s data breach, you could be a victim of identity theft. Hackers often sell stolen personal details on the dark web.
To monitor if you’ve been hacked or if your information has been leaked in a data breach, consider specialized privacy protection. Avast BreachGuard is an identity theft protection solution that safeguards your private information 24/7. We continuously scan the dark web, where hackers buy and sell leaked personal data. If your info is detected, we’ll contact you immediately so you can secure your accounts to prevent identity fraud.
Hackers are like lions: they prey on targets they’ve identified as least able to defend themselves. By taking a few quick preventative measures, you can make it much harder for a hacker to breach your updated defenses — and they’re likely to move on to an easier target.
Use a unique password for every account. If a hacker gets one, they’ll have only that one. Though they’ll try that password on all your other accounts, if it’s a strong and unique password, it won’t get them anywhere.
Update your software. Outdated software is vulnerable software, but current software is much less so. Use auto-update for all your devices, programs and apps, and get a driver updater for your PC.
Don’t click on ads or strange links. Hackers can seed ads with malware in a technique known as “malvertising.” They can do the same with infected websites to perform “drive-by downloads” of malware onto your device when you visit those sites. Click only on things you know and trust.
Look for HTTPS encryption. Checking for HTTPS is one of the easiest ways to check if a website is safe. If a site is using this secure protocol, you’ll see a little padlock icon in your browser’s address bar, and the URL will begin with “HTTPS.” Don’t enter personal details on any site that still uses plain old HTTP.
Change the default username and password on your router and smart devices. Give hackers at least a bit of a challenge when it comes to cracking your home network. Your first step when setting up a new router or smart device should be to change its login credentials.
Don’t do anything personal on public computers. Use them for generic searches, and that’s it. Don’t log into your personal accounts, as there might be spyware on the machine.
With the above tips in place, you can now take a longer-term focus on insulating yourself against hacking attempts. The following behavioral changes and software suggestions will go a long way toward protecting you from hackers.
![]() Download from first-party sources. On mobile, that’s the App Store and Google Play. On a PC or laptop, that means downloading directly from the developer’s website. When installing new programs, look out for any additional software that’s been bundled in. If you can’t choose to omit those bloatware programs, ditch the whole thing.
Download from first-party sources. On mobile, that’s the App Store and Google Play. On a PC or laptop, that means downloading directly from the developer’s website. When installing new programs, look out for any additional software that’s been bundled in. If you can’t choose to omit those bloatware programs, ditch the whole thing.
![]() Install antivirus software. A good free antivirus tool will defend you from a lot more than just viruses. You’ll be protected against the full range of malware in addition to other security holes such as out-of-date software, malicious downloads, and misbehaving programs. Shop around and select a tool with the right set of features to cover all your needs and devices. Some, like Avast One, are available for free, while others must be purchased.
Install antivirus software. A good free antivirus tool will defend you from a lot more than just viruses. You’ll be protected against the full range of malware in addition to other security holes such as out-of-date software, malicious downloads, and misbehaving programs. Shop around and select a tool with the right set of features to cover all your needs and devices. Some, like Avast One, are available for free, while others must be purchased.
![]() Get a VPN and use it. A VPN is a private internet tunnel from your device to the internet. It encrypts your traffic from your device to the VPN server, which means that no one outside your VPN provider can see what you’re doing. If you’re on unsecured public Wi-Fi, such as that in a cafe or shopping mall, protect yourself with a reliable VPN like Avast SecureLine VPN. Otherwise, your data is wide open for others to view.
Get a VPN and use it. A VPN is a private internet tunnel from your device to the internet. It encrypts your traffic from your device to the VPN server, which means that no one outside your VPN provider can see what you’re doing. If you’re on unsecured public Wi-Fi, such as that in a cafe or shopping mall, protect yourself with a reliable VPN like Avast SecureLine VPN. Otherwise, your data is wide open for others to view.
![]() Jailbreak your mobile device with extreme caution. Mobile devices, whether on iOS or Android, come with certain built-in security features and restrictions that help to prevent hacking. Some users prefer to bypass those limitations in order to obtain total control over their devices. If that interests you, be absolutely sure you know what you’re doing. Jailbreaking devices makes them extremely vulnerable to intrusion if they’re not properly protected — and likely voids your warranty as well.
Jailbreak your mobile device with extreme caution. Mobile devices, whether on iOS or Android, come with certain built-in security features and restrictions that help to prevent hacking. Some users prefer to bypass those limitations in order to obtain total control over their devices. If that interests you, be absolutely sure you know what you’re doing. Jailbreaking devices makes them extremely vulnerable to intrusion if they’re not properly protected — and likely voids your warranty as well.
![]() Don’t log in as an admin by default. Reserve administrative privileges for special cases, and set your default account permissions as a standard user. That way, if you accidentally click or download something malicious, the hacker won’t have free rein over your device.
Don’t log in as an admin by default. Reserve administrative privileges for special cases, and set your default account permissions as a standard user. That way, if you accidentally click or download something malicious, the hacker won’t have free rein over your device.
![]() Use a password manager. We’ve already discussed the importance of having unique passwords for all your accounts. Rather than keeping a log of all these passwords — a very bad idea, security-wise — use a password manager. Find a secure password manager from a reputable developer, since you’ll be entrusting it with all your digital keys. And try to find one that also offers password generation and multi-device sync.
Use a password manager. We’ve already discussed the importance of having unique passwords for all your accounts. Rather than keeping a log of all these passwords — a very bad idea, security-wise — use a password manager. Find a secure password manager from a reputable developer, since you’ll be entrusting it with all your digital keys. And try to find one that also offers password generation and multi-device sync.
![]() Related: do not store passwords in your browser. That is way less secure than a dedicated password manager. Many password managers are available as browser extensions with auto-fill capabilities, which provide the same convenience with far greater protection.
Related: do not store passwords in your browser. That is way less secure than a dedicated password manager. Many password managers are available as browser extensions with auto-fill capabilities, which provide the same convenience with far greater protection.
![]() Use two-factor authentication wherever you can. You won’t go wrong by having the additional layer of security that 2FA provides. Use it on your email, on your socials, on your banking accounts, anywhere you can. It’s not bulletproof — some clever phishing campaigns have started to take advantage of it — but overall, it’s a security upgrade that you’re better off with than without.
Use two-factor authentication wherever you can. You won’t go wrong by having the additional layer of security that 2FA provides. Use it on your email, on your socials, on your banking accounts, anywhere you can. It’s not bulletproof — some clever phishing campaigns have started to take advantage of it — but overall, it’s a security upgrade that you’re better off with than without.
![]() Lock down your online presence. The more information hackers can obtain about you, the more prepared they will be to phish you, guess your security questions, or commit fraud in your name. Consider restricting your social content only to your current contacts, such as by making your Facebook private and locking down your settings on Instagram. And don’t accept requests from random strangers. Also, think twice about using a social profile to log into another website or service. That’s just one more potential hacking opportunity that you could easily eliminate by quickly creating a separate account on that platform instead.
Lock down your online presence. The more information hackers can obtain about you, the more prepared they will be to phish you, guess your security questions, or commit fraud in your name. Consider restricting your social content only to your current contacts, such as by making your Facebook private and locking down your settings on Instagram. And don’t accept requests from random strangers. Also, think twice about using a social profile to log into another website or service. That’s just one more potential hacking opportunity that you could easily eliminate by quickly creating a separate account on that platform instead.
![]() Read app permission requests closely. Some app developers may get greedy and request more permissions than they need for their apps to function properly. Evaluate app permission requests carefully, and consider whether the developer is asking for too much. Be especially skeptical of apps that want to access your camera, contacts, microphone, or location information without a legitimate reason.
Read app permission requests closely. Some app developers may get greedy and request more permissions than they need for their apps to function properly. Evaluate app permission requests carefully, and consider whether the developer is asking for too much. Be especially skeptical of apps that want to access your camera, contacts, microphone, or location information without a legitimate reason.
![]() Brush up on anti-phishing techniques. Phishing and pharming are two of the most common techniques hackers use to get access to your info and accounts. Use a web browser with anti-phishing protection. Don’t provide or “verify” login credentials or personal information if asked — this common phishing tactic is surprisingly effective if wielded cleverly. And always scrutinize a website to make sure it’s legitimate before you enter any info. Check for spelling or grammar mistakes and verify that the entire site is complete, including the terms & conditions or contact pages. Hackers who make imitation phishing websites often miss those details.
Brush up on anti-phishing techniques. Phishing and pharming are two of the most common techniques hackers use to get access to your info and accounts. Use a web browser with anti-phishing protection. Don’t provide or “verify” login credentials or personal information if asked — this common phishing tactic is surprisingly effective if wielded cleverly. And always scrutinize a website to make sure it’s legitimate before you enter any info. Check for spelling or grammar mistakes and verify that the entire site is complete, including the terms & conditions or contact pages. Hackers who make imitation phishing websites often miss those details.
The world of hacking is vast. And with so many hacking methods out there, there’s no such thing as a catch-all remedy to the entire problem. If you can focus on the most prevalent sources of hacking — malware and phishing — you’ll make yourself a far less attractive target.
Hackers use malware to hack, and they hack in order to put malware on your device. Avast One is continually updated to protect you in real time against current malware threats, right as they emerge. It’ll detect, block, and remove malware and phishing attempts while also securing your data with a VPN, protecting valuable files against ransomware, and so much more.
Join hundreds of millions of people worldwide in protecting your data with industry-leading Avast security software.
Download free Avast One to defend against hacking and protect your PC against viruses & other threats in real time.
Install free Avast One to defend against hacking and protect your Android phone against viruses and other threats in real time.
Install free Avast One to defend against hacking and protect your iPhone against viruses and other threats in real time.
Download free Avast One to defend against hacking and protect your Mac against viruses & other threats in real time.
Protect your Android against hacking and malware with Avast One
Protect your iPhone against hacking and malware with Avast One