Protect your iPhone against threats with Avast One
- Security
- Privacy
- Performance
Ransomware is one of the defining cyberthreats of our time — and it’s showing no signs of slowing down. In recent years, hackers and other threat actors have unleashed a significant number of attacks, devastating the critical systems of a variety of organizations around the world, with the Colonial Pipeline attack and its long-term impact on fuel supplies in the US making headlines worldwide.

Here, we’ll look at where ransomware comes from and why it’s become so popular with cybercriminals. We’ll examine some of the most notorious recent ransomware attacks and see what organizations can do to shore up their systems.
We’ll find out which companies have paid up to $40 million to ransomware hijackers, discover why Russian-based companies tend to avoid being attacked, and learn why hospitals, tech companies, and government organizations are the most popular targets.

This Article Contains:
Ransomware is a type of malware that locks up your data or your device, then demands that you pay a ransom to get it back. But despite its recent boom in popularity, ransomware’s roots reach back decades.
One of the earliest instances of ransomware was the 1989 AIDS Trojan horse attack. Hosted on a floppy disk and distributed to attendees of an AIDS conference, the AIDS Trojan encrypted various files on a targeted hard drive, then instructed victims to send $189 to a PO Box in Panama. Fortunately, the encryption was easy to reverse.
Since then, ransomware has become far more sophisticated. Here are some of the most destructive ransomware strains witnessed in recent years:
CryptoLocker (2013)
CryptoLocker emerged in September 2013 and wreaked havoc across the world until it was finally neutralized in May 2014 by an international cybersecurity task force. CryptoLocker was so effective in part due to its spread via the massive Gameover ZeuS botnet.
Cerber (2016)
Cerber is a game-changing type of ransomware that popularized the RaaS (ransomware-as-a-service) model, where hackers “rent” out their ransomware for others to use in exchange for a percentage of the takings.
Locky (2016)
Focusing mostly on healthcare institutions, Locky’s attacks began in 2016 and continued throughout the year. Avast’s threat intelligence team was able to examine Locky’s code, linking it to the hacking collective known as Dridex.
Petya (2016) & NotPetya (2017)
First appearing in 2016, the Petya family of ransomware is most notorious for its NotPetya strain, which blew up with a surge of attacks in 2017. This single wave resulted in over $10 billion in damages across Europe and the US.
WannaCry (2017)
The WannaCry ransomware attacks of May 2017 were incredibly potent, over 230,000 computers across 150 countries were infected in a single day. The resulting damage and cleanup costs rose to an estimated $4 billion.
DarkSide (2020)
The DarkSide group’s RaaS was responsible for many of the biggest ransomware attacks and demands in 2020 and 2021. Darkside actors claim to avoid government and healthcare targets in favor of high-value corporations, but the group was behind the 2021 Colonial Pipeline attack that crippled fuel supplies across the East Coast of the US.
The remarkable rise of ransomware attacks in recent years can largely be attributed to one factor: the introduction of RaaS, or ransomware-as-a-service. Under this system, a developer creates a strain of ransomware, then licenses it to other cybercriminals for use in their attacks. As such, the RaaS model has two primary benefits for hackers:
The ransomware developer no longer has to worry about carrying out attacks. They instead earn money by collecting a percentage of each attack’s revenue.
Ransomware attackers don’t need nearly as much technical expertise. The “plug-and-play” RaaS model allows attackers to focus solely on infecting victims and collecting payments.
Avast’s Threat Labs found that ransomware attacks in the third quarter of 2021 were 5% higher than in the previous quarter, and a towering 22% higher than in the first three months of the year.
While ransomware developers and attackers benefit, victims are losing more than ever. Compared to the AIDS Trojan’s ransom demand of $189, today’s payments are massive. When large corporations are targeted with ransomware, it’s not unusual for the demands to reach millions of dollars.
For a better idea of what the current situation looks like, we’ve broken down the ransomware landscape into several categories:
The data in the following sections is sourced primarily via the public collection available at Information Is Beautiful. Not every organization hit by an attack reports it (or the cost) — perhaps fearing damage to their reputation — so the data below may be incomplete. But general trends are worth highlighting.
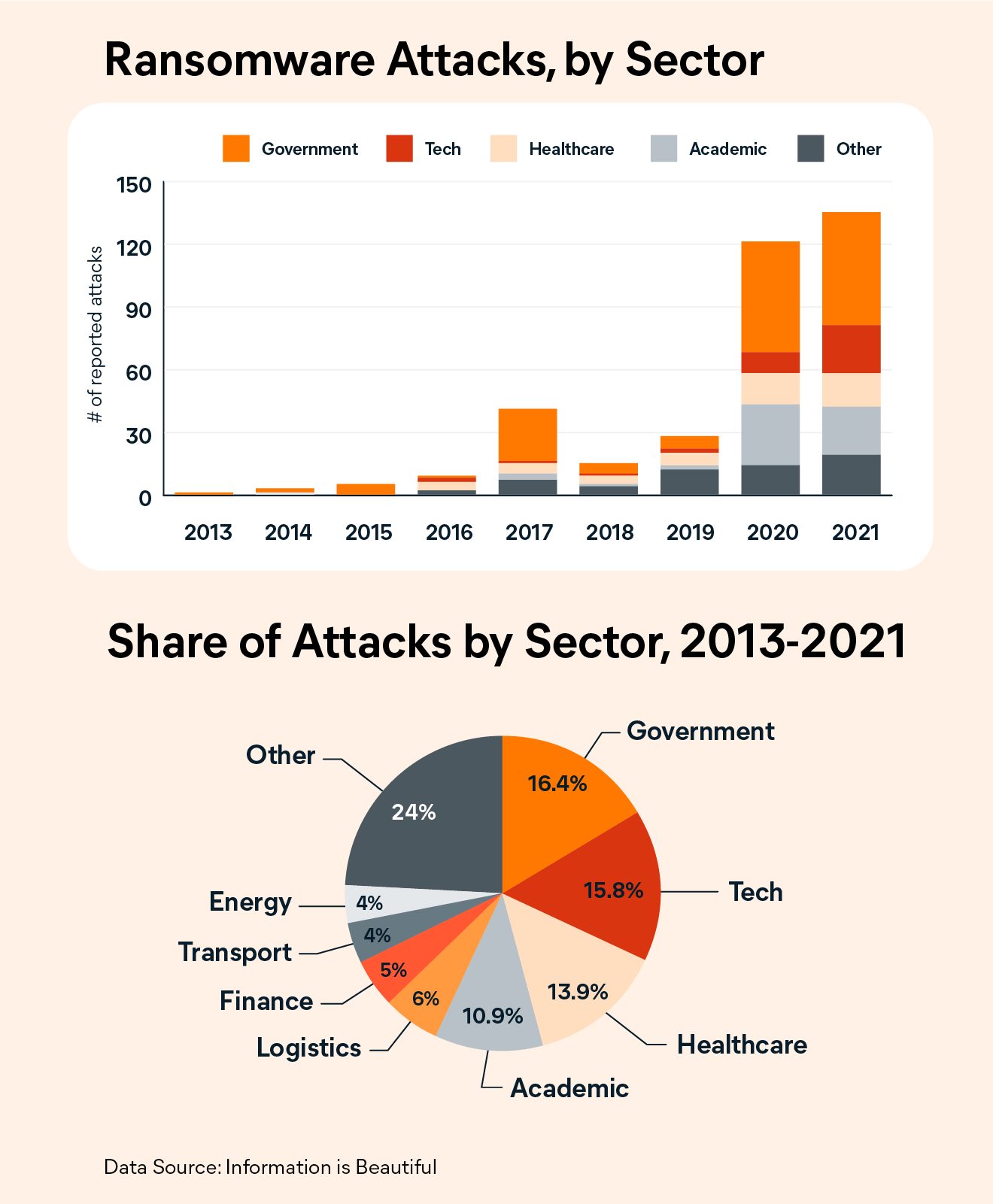
Not only can ransomware cripple a company’s operations, it’s also a growing scourge. Whereas the 2010s saw fewer than 15 publicly reported ransomware attacks on businesses and other organizations annually, there were an astonishing 135 reported attacks in 2021 (see chart below).
While attacks overall have been on the rise, certain sectors of the economy are more frequently targeted. In particular, government, technology, healthcare, and academic institutions have absorbed the bulk of attacks. Of all the reported attacks looked at, those four sectors alone account for 57% of all attacks.
During this time, the tech sector has come under increasing threat. From 2017 to 2019, only 7% of reported ransomware attacks targeted tech companies. Over the past two years, that share has jumped to over 20%.
While attacks on government institutions are often politically motivated, hackers attacking tech and healthcare organizations may perceive these groups as being more likely to pay. Additionally, our own research has found that hospitals and healthcare providers may lack the budget needed to keep their systems updated, leaving their security infrastructure more vulnerable.
Here’s a look at the most common ransomware targets, broken down by year and sector.
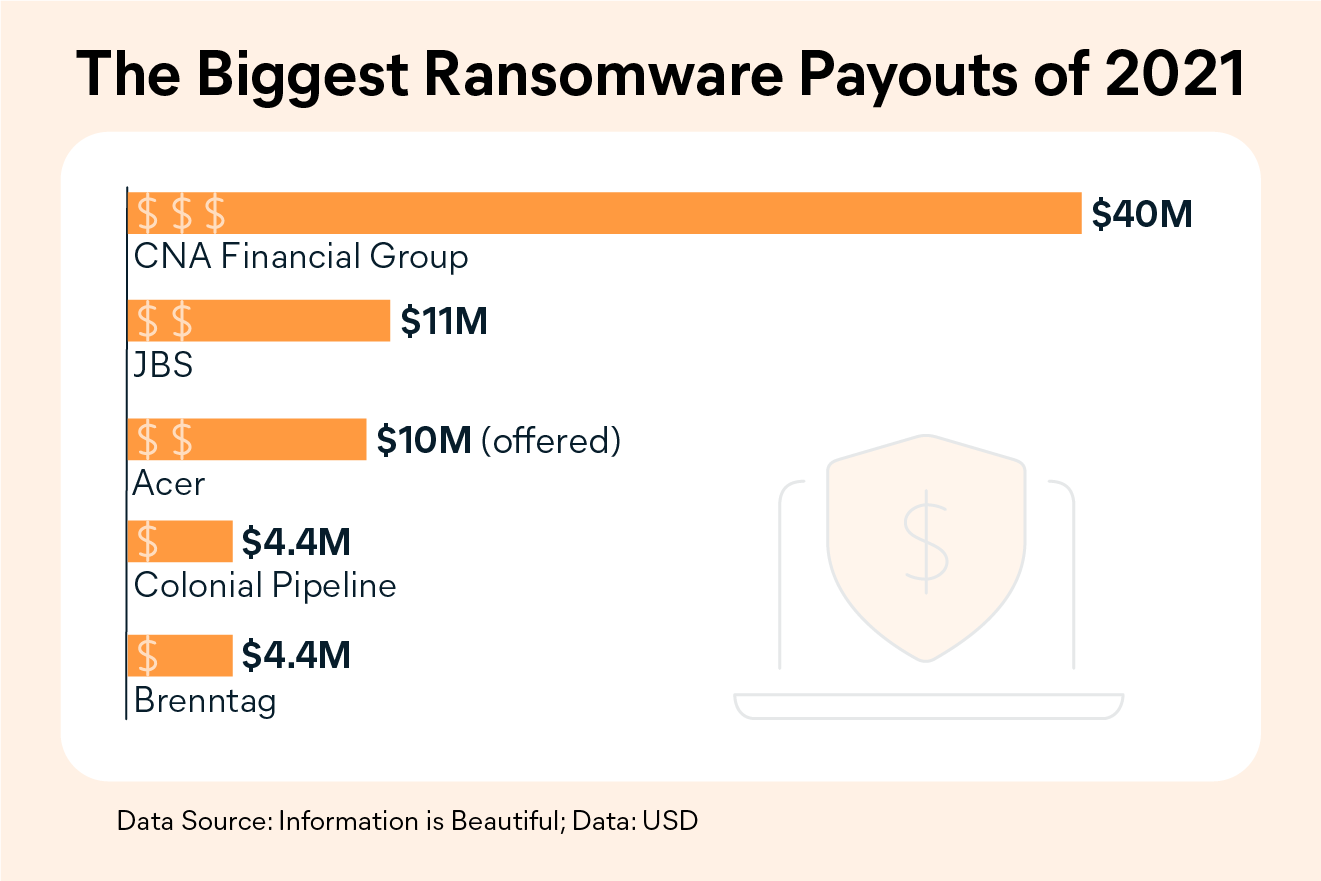
2021 was a important year for ransomware. While most companies choose not to disclose ransomware payments, some victims did make this information public. Doing so can help showcase the dangers of ransomware while helping the authorities and cybersecurity researchers in their fight against it.
CNA Financial Group: $40 million
Two weeks after a massive data breach, Chicago-based insurer CNA Financial Group paid a staggering $40 million to ransomware hackers in March 2021.
The hackers used a strain of ransomware known as Phoenix Locker, reportedly developed by Russian cybercrime organization Evil Corp. In 2019, the FBI issued a $5 million reward for information leading to the arrest of the group’s alleged leader.
JBS: $11 million
After an attack in May 2021 that shut down operations in the US and Australia, JBS — the world’s largest beef supplier — paid cybercrime organization REvil an $11 million ransom.
JBS claimed that while it was able to restore the majority of its systems without help, the payment was made to ensure the stolen data would not be leaked.
Acer: $10 million (offered)
In March 2021, REvil — responsible for many recent ransomware attacks until its abrupt disappearance in the middle of last year — slammed PC manufacturer Acer with a $50 million ransomware demand.
In response, Acer’s negotiators reportedly offered to pay $10 million, which the hackers declined. Acer’s servers in India were hit with a second cyberattack in October 2021, this time the data theft came at the hands of the Desorden Group.
Colonial Pipeline: $4.4 million
The Colonial Pipeline is the largest pipeline system in the US for refined oil and can transport up to 3 million barrels per day between New York and Texas. So when it was hit with a DarkSide RaaS attack on May 7, 2021, it made worldwide news.
Colonial Pipeline quickly chose to pay, but not before fuel shortages spread across the southeastern US, with hours-long queues forming at gas stations throughout the region. The US Department of Justice announced a month later that it had successfully recovered approximately $2.3 million of the ransom.
Brenntag: $4.4 million
Leading German chemical supplier Brenntag paid its own $4.4 million ransom to an attacker using DarkSide RaaS in May 2021. The ransomware attack targeted the group’s North American servers, and the hackers claimed to have captured over 150 GB of data.
The attackers claimed to have breached Brenntag’s systems with the use of stolen credentials, though they denied having stolen the credentials themselves.
DarkSide and other ransomware attackers often choose to target large organizations with the perceived ability to meet millions of dollars in ransom demands. The biggest ransomware victims of 2021 aren’t local hospitals or government agencies, but large multinational companies.
Toyota ($256.7 billion)
Japanese auto manufacturer Toyota was hit with two ransomware attacks in 2021: one against its Daihatsu Diesel Company subsidiary in Europe and another against its subsidiary Auto Parts Manufacturing Mississippi.
JBS ($270.2)
As described above, international meat supplier JBS paid the REvil group a ransom of $11 million after a May 2021 attack.
Shell (183.2 billion)
A March 2021 ransomware attack saw the Dutch giant Shell targeted by the Clop ransomware group. The attack focused on the Accellion file-sharing service used by Shell to transfer large amounts of data.
AXA ($109.6 billion)
In an ironic twist, French insurance provider AXA suffered a ransomware attack shortly after announcing that it would no longer provide ransomware coverage for its policyholders.
Kia Motors ($50 billion)
Reports emerged in February 2021 that Kia Motors America had suffered service outages due to a ransomware attack from the DoppelPaymer group. However, both Kia as well as its parent company Hyundai have denied that any such attacks occurred.
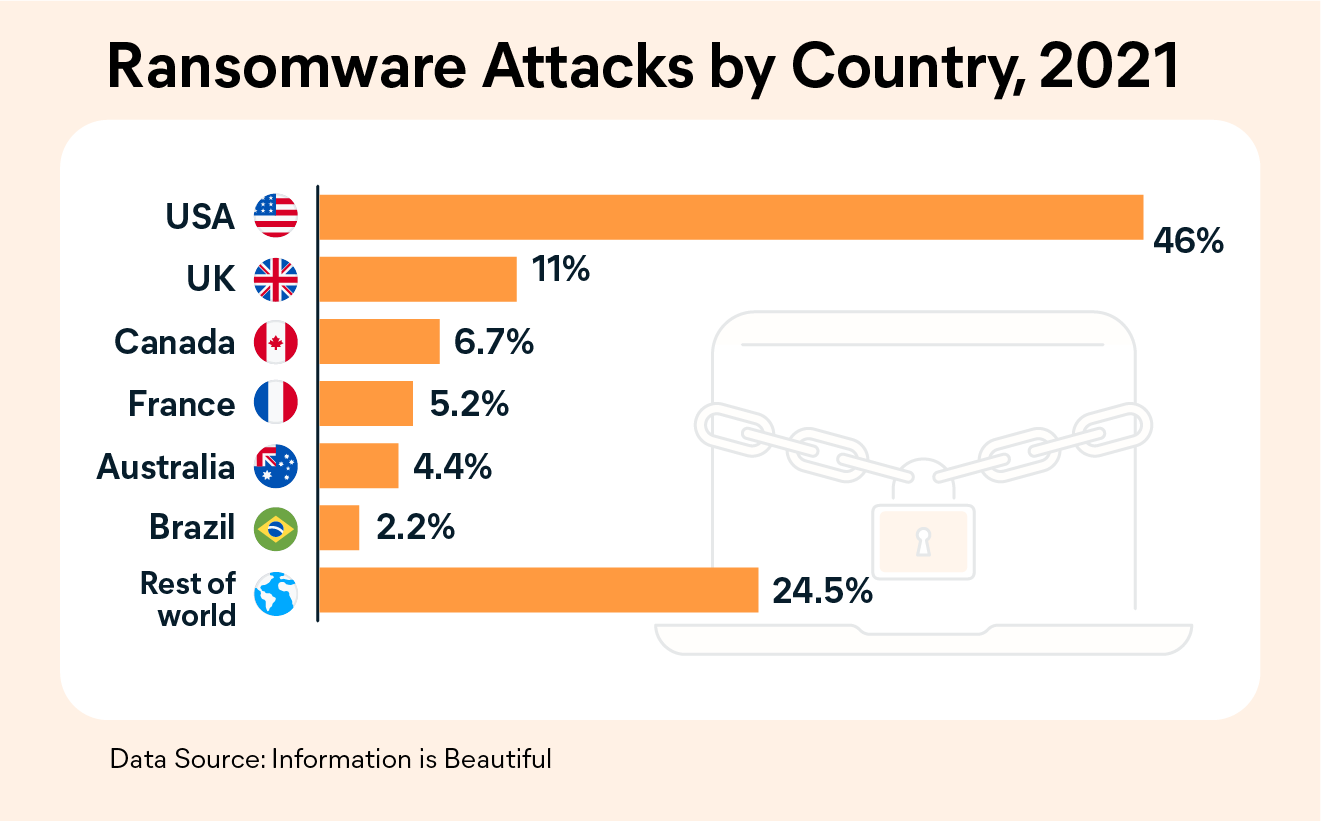
Ransomware attacks happen all over the world, but organizations in the US are targeted more often than those headquartered anywhere else. Many of the top ransomware groups are alleged to be based out of Russia and other Eastern European countries, and they tend to avoid targeting victims in their region. This is due to the belief that the Russian government typically declines to pursue cybercriminals who only attack foreign targets.
That might be why many strains of ransomware developed in Russia or Eastern Europe include built-in failsafes that disable the malware if it detects that it’s running on a machine in Russia or another member of the Commonwealth of Independent States.
Large-scale ransomware attacks can result in near-total organizational shutdowns, and it can easily feel as though paying the ransom is the best way to get things back to normal. However, our advice is clear: never pay the ransom. Here’s why:
You can’t be sure that it’ll work.
Though cybercriminals may promise to return your data, there’s no guarantee that they’ll actually follow through. It’s impossible to know what will happen until you pay — and you might find that your data is still locked. It might not even be possible to decrypt your data either way. Some variants of the Petya ransomware family are irreversible.
You’re encouraging future attacks.
When victims pay ransoms, it “proves” to the attacker that ransomware works. Ransomware developers and hacking groups can use their gains to fund the development of better software and more destructive methods of attack.
Some ransomware attacks can be a literal matter of life and death. Ransomware attackers leverage this urgency when they target hospitals, public utilities, and similar institutions. It may not always be possible to withstand an attack and wait for the ransomware to be decrypted.
For that reason, while the FBI urges victims not to pay, it also sympathizes with those who have. Many companies are reluctant to disclose cyberattacks, but doing so can help authorities in their fight against ransomware and other cybercrimes.
Ransomware needs an entry point to attack a network. Whether that’s a security weakness in outdated software, a weak password, a stolen login credential, or even a gullible employee, cybercriminals will find a way to exploit the vulnerability and get their ransomware inside. Increasingly, attackers have even recruited employees to gain inside access to a targeted organization’s internal systems.
Phishing emails
Phishing attacks are emails and other communications designed to trick someone into disclosing sensitive personal data or opening a malicious file.
Spear-phishing campaigns target specific individuals, while whaling attacks are directed at high-worth individuals such as C-suite executives. Malicious emails have increased by 600% during the ongoing COVID-19 crisis.
Remote Desktop Protocol
Microsoft’s Remote Desktop Protocol (RDP) allows network admins to easily access devices on their networks. But with the right login credentials, hackers can do the same.
Legitimate admin credentials may be obtained via phishing, data breaches, brute-force cracking, or credential stuffing (using known username/password combinations across other login portals). Making remote access available only through a VPN connection, and not exposing it to the entire internet, is one way companies can better protect against RDP vulnerabilities.
Software vulnerabilities
Hackers exploit vulnerabilities in outdated software to breach unprotected systems and servers — including corporate VPN servers — and install ransomware. Using current software is the best way to close off this type of ransomware attack vector.
Some ransomware gangs have pulled in so much money, they’re wealthy enough to purchase zero-day vulnerabilities, which are newly discovered weaknesses that remain unknown to the software’s developers. Cyberattacks leveraging these security flaws are called zero-day exploits.
How solid are your cybersecurity basics? Take our cybersecurity quiz and find out.
Preventing ransomware attacks requires vigilance from organizations and individuals alike. Organizations must secure their networks against intrusions while training staff to recognize phishing attacks. Meanwhile, everyone can protect against ransomware by following a few basic cybersecurity tips.
Implement cybersecurity training
Give your team the skills and knowledge they need to defend against ransomware. Teach employees to use strong passwords and recognize phishing attacks and malicious links. Then make sure everyone knows how to report suspicious emails or other questionable activity.
Have a plan
The way you react to a ransomware attack can heavily determine the outcome of the event. Create a ransomware attack plan — or a business continuity plan — so that everyone is prepared ahead of time.
Back everything up
Ransomware that works by encrypting data relies on you not having any other copies of that data for leverage. With secure backups, you can continue accessing and using all your data even while the attack is ongoing. Store your backups in the cloud or in an offline external storage device to prevent the ransomware from reaching them.
Use layered security
One type of security alone may not be enough to block ransomware from all angles. But a layered security approach that includes network security, endpoint protection, data security, and more will cover your organization from all angles.
Always update and patch
Update your organization’s software and hardware to protect against vulnerabilities. Automate the update process whenever possible — configure employee devices to update automatically, and consider a security tool that automatically downloads and installs software updates and manages patches whenever they’re released.
Learn more about cybersecurity solutions to keep your business protected.
Back up your data
Back up your sensitive data or clone your hard drive to the cloud or an external offline storage device. This will prevent ransomware from reaching your backups and encrypting them.
Use current software
Install updates for your operating system and all your apps whenever they are available to close off any pre-existing security weaknesses.
Don’t open unexpected email attachments
Ransomware is often spread through malicious attachments in phishing emails. Never open attachments from senders you don’t know. If you receive an attachment from a trusted contact, get in touch with them directly to verify that they sent it to you. It’s possible that their email address might have been spoofed.
Be skeptical of links
Phishing emails may include links to malicious websites, as can online forums and comment sections. Use caution when clicking strange links. To be extra-safe, manually enter the URL you’d like to visit.
Don’t enter any data into unsecured websites
Before logging in or entering any personal data into an online form, verify that the website is safe and protected with HTTPS security. You’ll see a padlock icon in the address bar of your browser — click it to verify the website’s security and certificates.
Download software only from official sources
Source new software directly from the manufacturer or from first-party portals like the Apple App Store. Unofficial software downloads on third-party platforms may be Trojans in disguise that can infect you with ransomware.
Protect your devices with security software
Antivirus software is the best way to defend against ransomware. Install an anti-ransomware tool on your devices to automatically detect and block ransomware before it can infect your devices. Also consider adding a firewall to your home Wi-Fi network, if your router doesn’t automatically have one.
Ransomware can’t hurt you if it can’t find you. A strong cybersecurity app will block viruses and malware before they have a chance to infect your device. With strong security measures set up at all possible attack vectors, Avast One will protect you from ransomware and other malware, unsafe links, harmful downloads, unsecure websites, and more.
Get 24/7 protection so you never even have to think about paying a ransom.
Download free Avast One to block ransomware and other malware. Get real-time protection for your PC.
Install free Avast One to defend your iPhone against online threats. Get real-time protection.
Download free Avast One to block ransomware and other malware. Get real-time protection for your Mac.
Install free Avast One to block ransomware and other malware. Get real-time protection for your Android phone.
Protect your iPhone against threats with Avast One
Protect your Android against ransomware with Avast One