Get enterprise-grade security for your business with Avast Business Hub
- Security
- Privacy
- Performance
Cybersecurity (or IT security) is the practice of protecting critical data across devices, networks, and programs from unauthorized access and attacks. Cybersecurity protects systems against hackers and others trying to exploit vulnerabilities and infiltrate computer networks. Learn what cybersecurity means, the most common threats, and how comprehensive threat-detection software can safeguard your data against cyberattacks.
 - SMB/What-is-cybersecurity-Hero.jpg?width=1200&name=What-is-cybersecurity-Hero.jpg)
Effective cybersecurity uses a combination of tools, technologies, and practices to protect critical digital infrastructure — even if the cyber threats come from within an organization. To secure computer networks and other critical systems, a few small steps can make a big difference in protecting yourself and your business.

This Article Contains:
The purpose of cybersecurity is to combat cybercrime, such as the use of malicious software, theft of sensitive information, extortion, and business disruption. Cybersecurity practices prevent cyberattacks that aim to target individuals’ or businesses’ important information.
Though related, cybersecurity and information security cover slightly different areas. Information security is concerned with protecting data in any form from any threat, digital or physical. Cybersecurity focuses on computer systems and protecting data from unauthorized digital threats, like cyberattacks. Cybersecurity can be understood as a form of information security.
Here are the main types of cybersecurity and how they work:
Network security safeguards your internal computer networks and protects both hardware and software. It prevents threats like hackers from compromising your network or malware from infecting your system. Network security tools include antivirus and anti-malware software, firewalls, and virtual private networks (VPNs).
Application security increases the security of apps and programs by removing vulnerabilities. Most application security is done at the development stage, but updates and patches are also released after apps launch. To ensure robust application security, use a patch management tool to check for patches and updates and install them as soon as possible.
Endpoint security protects all devices connected to your network — desktops, laptops, servers, printers, phones, etc. The goal of endpoint security is to protect against cyber threats like unauthorized access, data breaches, malware, and ransomware. Common endpoint protection solutions include antivirus software, VPNs, and anti-phishing email scanners.
Data security refers to the policies, processes, and technologies that prevent data from being modified, destroyed, or disclosed — whether accidentally or maliciously. Examples of data protection practices include strong passwords, regular system backups to aid data recovery, and encryption to secure data against unauthorized access.
There are many types of cybersecurity threats — malware, phishing, DDoS attacks, and SQL injection, just to name a few. Here are some of the most common cyber threats:
Malware refers to the full range of malicious software — from viruses, worms, and trojans to spyware, ransomware, and rootkits. Malware is often unintentionally installed or downloaded, often by opening infected email attachments or clicking on malicious links. Once it gets it, malware can often go about its sinister business undetected.
WannaCry is a famous example of malware — more specifically ransomware — that wreaked havoc worldwide. In 2017, WannaCry hijacked computers running Microsoft Windows and demanded a Bitcoin ransom to decrypt them. More than 200,000 computers in over 150 countries were infected. Sadly, ransomware attacks continue to cause chaos around the world.
SQL injection is a common hacking technique used by cybercriminals to insert malicious code into a website or app to access and manipulate private information stored in a database. The target usually includes users’ login credentials, which allow the hacker to impersonate the user or sell the stolen information. Preventing an SQL injection attack requires specific knowledge of website development.
The aim of a denial of service or distributed denial-of-service (DDoS) attack is to cause a website, machine, or network to crash. DDoS attacks flood targeted networks with requests — often through botnets — until the network becomes overwhelmed and can no longer serve additional users, resulting in a denial of service.
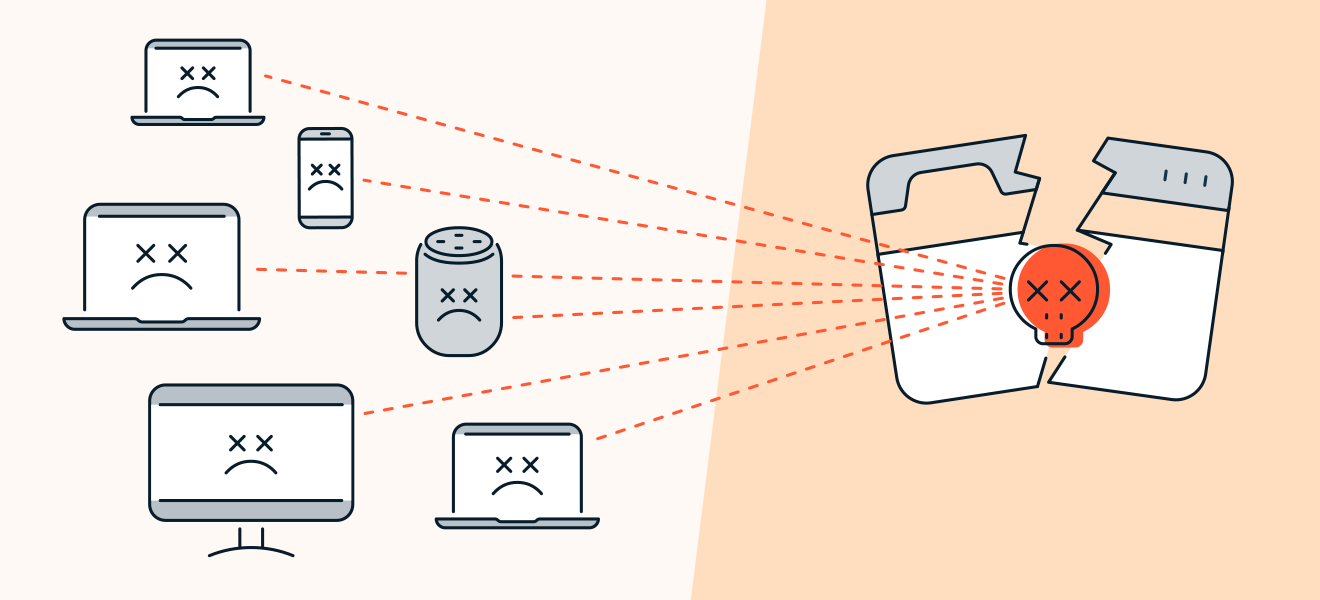 Denial of Service (DoS) attacks flood a server with traffic until it crashes — making it unable to serve its regular users.
Denial of Service (DoS) attacks flood a server with traffic until it crashes — making it unable to serve its regular users.
A man-in-the-middle attack happens when two users are communicating while a third party — the man in the middle — intercepts the communication, often by spoofing. The aim of a man-in-the-middle attack is to steal data or impersonate the victim, while the victim remains unaware that an attack is taking place.
Cybercriminals may create a fake, pharming website, and then persuade a user to log in by sending an email pretending to be the legitimate owner of the store. When the user logs in, they unintentionally hand over their credentials to the cybercriminal. An evil twin attack works in a similar manner, but instead of a website attackers create a fake Wi-Fi network.
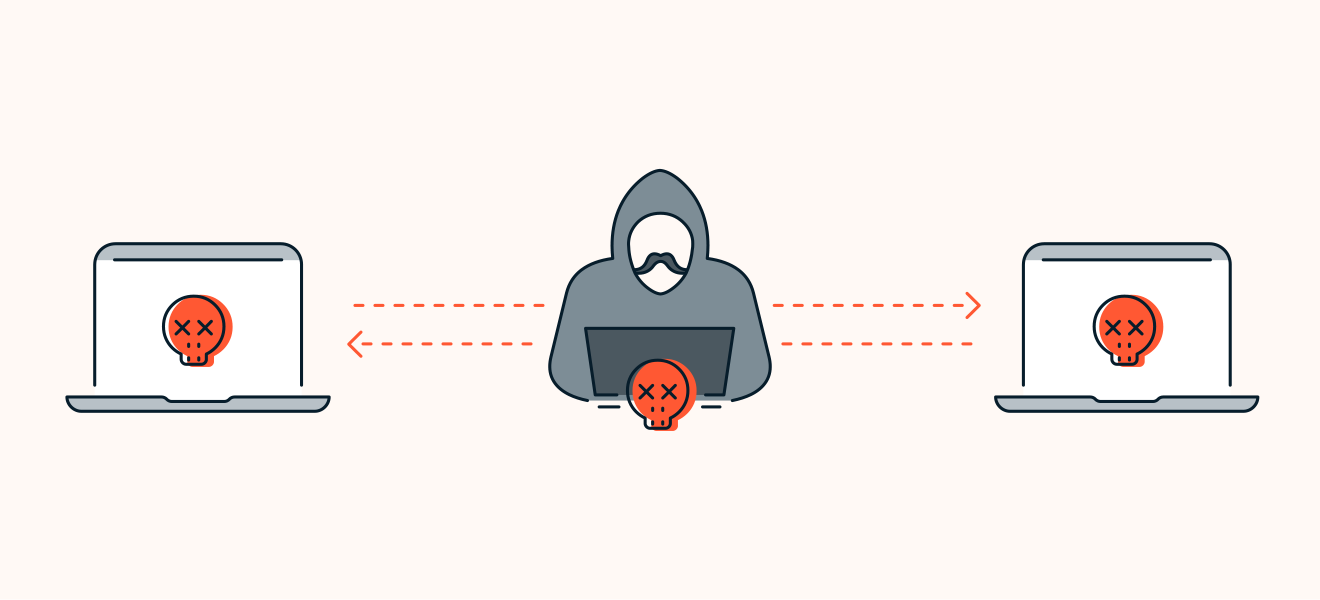 During man-in-the-middle attacks, hackers intercept communications between two devices.
During man-in-the-middle attacks, hackers intercept communications between two devices.
Cybersecurity protects critical system infrastructure and sensitive data from attacks, theft, and damage by cybercriminals. As cybersecurity threats have become more sophisticated, damaging, and costly for individuals as well as businesses, cybersecurity measures are more important than ever.
Today, cyberattacks are complex and threaten a variety of targets, impacting businesses, freelancers, and individuals alike. The number of attacks is also on the rise — since 2020, cyberattacks have increased by 31%.
The cost of a cyberattack can be severe — they’re often very expensive for organizations to clean up and inflict lasting reputational damage. Cyberattacks can cost millions of dollars to fix, result in devastating data loss, and leave companies scrambling to assure their customers that their systems are secure.
For small businesses in the UK, the average financial cost of a security breach in 2020 was £3,110 (US $4,185), while for medium and large firms, the cost was significantly higher. And after data is exfiltrated, it can end up on the dark web, accessible to a variety of shady actors.
It’s worth noting that regulatory requirements continue to evolve, with the aim of holding organizations more accountable for protecting their customers’ data. The General Data Protection Regulation (GDPR), which covers data use in the EU, lets regulators fine organizations up to €20 million (US $24 million) — or 4% of their annual global turnover — for violations.
Beyond the direct cost of a cyberattack, your business could experience reputational damage and a loss of credibility among current and potential customers.
Altogether, the growing risks mean that when storing and sharing data and sensitive information online, it’s vital to keep your cybersecurity knowledge up to date, and prioritize protective measures.
Reliable tools like the Avast Business Hub will help ensure your business’s critical infrastructure and data are protected. Sign up today for real-time threat monitoring.
Cybersecurity protects computer networks against cyberattacks, ensuring the safety of individuals’ and businesses’ critical data. Cybersecurity helps you and your business by:
Protecting against unauthorized user access
Minimizing business interruptions by eliminating threats
Improving confidence in your business, both externally and internally
Allowing your business to recover quickly after a data breach
Ensuring security best practices and legal and regulatory compliance
As cyber threats increase worldwide, so does the disinformation surrounding the importance of cybersecurity. Not taking cybersecurity seriously is just as threatening as the many active threats out there today. Here are a few common cybersecurity myths:
It won’t happen to us.
Cyber threats can happen in every industry, and are increasingly targeting more sectors — such as government agencies, healthcare industries, and even non-profits. Cyberattacks are also happening in new ways, through smart home devices (IoT) and cloud storage.
All our vulnerabilities are known.
New vulnerabilities like zero-day threats are reported all the time. That’s why apps and software developers constantly release updates, to ensure vulnerabilities are patched and users remain protected from exploits.
My company protects all my devices.
While this is hopefully true, human error — often as a result of a social engineering attack — is one of the most common causes of unintentional data breaches. Learning basic cybersecurity will help keep your devices — and your organization — protected against threats.
To shore up your cybersecurity, always update your devices, software, and operating systems whenever new updates are released. Use strong passwords, two-factor authentication, and reliable anti-malware tools.
Improved cybersecurity requires continuous attention to safeguarding all data stored by your business — thankfully, keeping up with cybersecurity best practices will make that easier.
Here are the best ways to instantly improve cybersecurity:
Software vendors regularly release updates and patches to fix vulnerabilities, but this also makes the vulnerability known to cybercriminals trying to exploit it. It’s critical to keep all your devices, operating systems, and software up to date.
Some password hackers use a technique called brute-forcing, where they attempt to gain access to your accounts by rapidly trying thousands of possible passwords. The stronger your password, the less likely they’ll succeed.
Use a different password for every account, website, or application you access. And use a password manager to keep track of them. A password manager encrypts and stores each of your passwords, allowing you to easily access them across all of your devices. You can also use it to generate random, secure passwords.
To add an extra layer of security to your accounts, use multi-factor authentication (MFA), which requires at least two factors of authentication to access a system. These factors can include passwords, PINs, facial or voice recognition, fingerprints, SMS messages, etc.
Cybercriminals can be quite sophisticated, which makes security an ongoing challenge. Educate yourself and your staff on the latest threats and cybersecurity best practices, such as avoiding suspicious email attachments and other phishing campaigns.
People are often the weakest link in successful cyberattacks. Those with an understanding of key cybersecurity basics can protect themselves and the company they work for. And companies that conduct regular penetration tests to find vulnerabilities will help reduce the risk catastrophic data breaches.
Here are the main cybersecurity technologies and best practices to start with:
Identity and access management (IAM)
This cybersecurity methodology includes single sign-on (SSI), multi-factor authentication (MFA), and privileged user accounts. IAM gives an organization greater visibility over threats that appear on devices they can only access digitally.
Security information and event management (SIEM)
SIEM helps organizations study, recognize, and prevent cyber threats and vulnerabilities before they cause harm. Artificial intelligence (AI) is now used widely in SIEM tools, which allows cybersecurity threat prevention without human action.
Comprehensive data security
A platform aiming to protect sensitive information across different environments is crucial. Any good data security platform will include real-time monitoring for vulnerabilities and threats across all environments, and it can back up and encrypt data to prevent data breaches.
Automation in cybersecurity
AI and machine learning have become integral for improving cybersecurity. Automation can help with threat detection and classification, automatic threat responses, and freeing up human resources.
The National Cyber Security Alliance (NCSA) recommends that corporate management take responsibility in preparing for inevitable cyber threats. The NCSA advises assessing cybersecurity risks by identifying three main areas:
An organization’s most valuable information or data that requires protection
The main risks or vulnerabilities threatening valuable data
The probable damage to the data or company should a data breach occur
After these areas are identified, consider any laws and regulations — such as GDPR, HIPAA, or FISMA — that affect the way your company collects, stores, and shares data.
Simply identifying these areas and creating a plan to detect and mitigate security incidents will considerably improve your organization’s cybersecurity.
Strong business antivirus software will protect your organization against a variety of threats. It will detect, block, and remove cyber threats — such as viruses, malware, and ransomware — before they can cause any harm. A comprehensive package should also include anti-spam and anti-phishing protection, a firewall, and browsing protection.
Cyberthreats are continually evolving, and your defenses should too. With the Avast Business Hub, you can be sure your business devices, data, and applications are protected in real-time. Monitor threats with the built-in dashboard and proactively secure your devices and software with automated patch management. It’s easy to use and optimized for business efficiency — start your free trial now.
Find the right cybersecurity solution for your business and protect your most important data on the go with the Avast Business Hub.
Find the right cybersecurity solution for your business and protect your most important data on the go with the Avast Business Hub.
Find the right cybersecurity solution for your business and protect your most important data on the go with the Avast Business Hub.
Find the right cybersecurity solution for your business and protect your most important data on the go with the Avast Business Hub.
Get enterprise-grade security for your business with Avast Business Hub
Get enterprise-grade security for your business with Avast Business Hub